Evgen verzun
Blog
May 2, 2023
Trust Wallet Extension Exploit: $170,000 Stolen So Far

Last week Trust Wallet users received some stressful news - close to $170,000 were drained from wallets due to the critical vulnerability in the back-end module WebAssembly (WASM).
The company stated that the exploit did not affect mobile app users, those of us who only imported wallet into the extension, or people who created the wallet somewhere around November 13 and November 23 in 2022.
What makes the situation bad though is that attackers could steal funds without any interaction from the targeted wallet owners.
Even though Trust Wallet has patched the hole, the fix only works for wallets created after November 23rd. So if you have created a wallet using the browser extension around the aforementioned dates, you might be in the risk group and would be advised to move your funds to a new wallet address.
I hope none of my readers were affected by this, and would like to dig deeper into this topic.
‘Trusted’ By 60 Million Devices
One thing we can all agree on is that the Binance-backed wallet is one of the most popular places to store crypto assets.
As mentioned in the description of the wallet in Chrome’s web store, it is installed on approximately 60 million devices. A truly staggering number, given that the extension was released just last November.
Trust Wallet delayed the announcement of the vulnerability to prevent more attacks and minimize potential breaches, which is a fairly popular approach among many companies who find themselves in a similar situation.
But just as it usually plays out, it took some big name researchers, in this case The Ledger Donjon team, to discover the vulnerability, describe it in detail, and make sure the issue was acknowledged publicly and fixed.
Ledger’s report is available for your reading pleasure, but if you want a simplified version of what occurred there, I might be able to help with that.
Flawed Seed Generation Is To Blame
You might think that randomness is a bad quality when we talk about crypto, but actually, unpredictability is vital when creating a new wallet.
Scientist and cryptography experts usually describe ‘randomness’ with a term ‘entropy’, which roughly means a measure of the number of possible arrangements a system can have.
The higher the entropy is, the more uncertain we are about the states making up the object. This effect is required to prevent anyone from being able to have any information on the generated sequence, since it’ll be the seed of all keys used by your wallet on all chains.
Sadly, Trust Wallet didn’t have quality entropy.
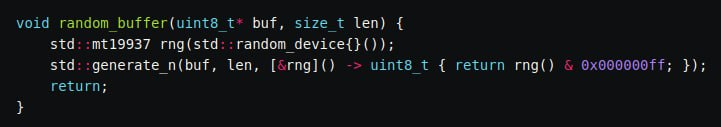
“What we do here is simple, we wrap std::random_device with std::mt19937 and return a random uint32 value, inspired by emscripten-core/emscripten#12240.”
The version of WASM that was affected utilized MT19937, a pseudorandom number generator (PRNG) with the total entropy of only 32 bits, allowing to create around 4 billion possible combinations. While 4 billion might sound like a big number, a single computer can generate all these mnemonics in just a couple of hours.
Ledger Donjon created a file containing all possible seeds, as described in their report.
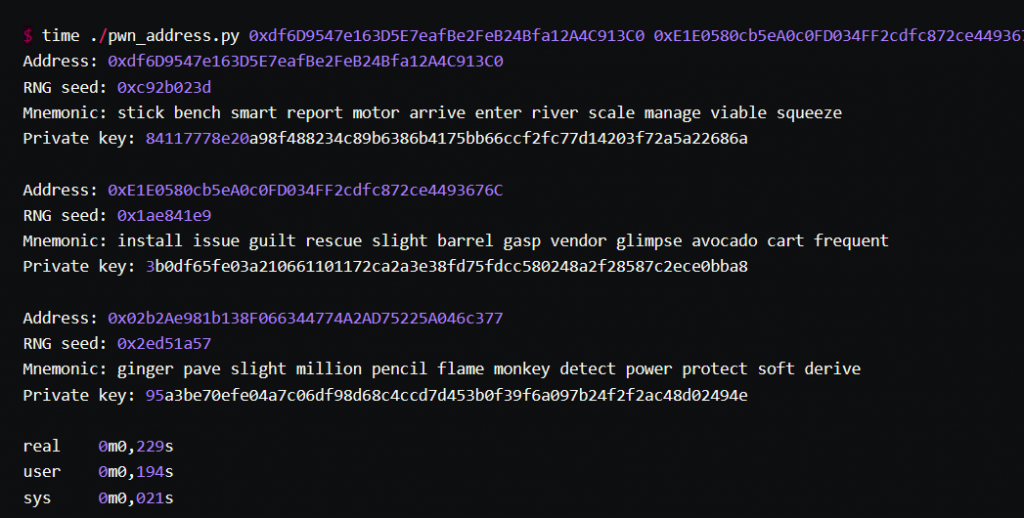
What’s even more fascinating is that providing mnemonics for vulnerable addresses took them about 0.2 seconds!
To summarize, skilled bad actors could compute all seeds and private keys, scan the related blockchains to extract all the used addresses, and get all the addresses of wallets created by Trust Wallet to steal funds.
Not an easy task, but certainly doable for those who know their stuff and want to get the cream.
Simply put, Mersenne Twister PRNG should not be used for cryptographic purposes and it has been unanimously discouraged for implementation. Almost $30 millions were at risk, but through the effort of Ledger’s security researchers, the nightmare scenario could be avoided.
But the danger of losing money is still lurking…
Vulnerable Addresses Still Have Around $88,000
Trust Wallet announced that it would create a reimbursement system that would notify impacted users via notifications through their browser extensions, and would refund all lost funds.
They have also urged the owners of all remaining vulnerable addresses to move their assets to new wallet addresses, since this exploit illustrates the worst possible scenario - accounts are compromised forever. Trust Wallet offered users customer support and to reimburse gas fees for transferring funds to uncompromised wallets.
Given the pressure and the complexity of contacting the targeted users, Trust Wallet did a good job. It’s in these tough moments when the company can show that it is competent at their job and transparent with their users. A security incident alone is not a disaster, but mishandling it is.
There has been a visible uptick in crypto exploits in 2023, with over 20 projects suffering attacks that led to the loss of user funds. The most notable attack of the year so far involved DeFi protocol Euler Finance, where close to $200 million were stolen.
The hacker returned $90 million a few days later., but still, there is a clear need for higher security standards in the crypto industry.
Donjon Ledger represents exemplary understanding of the issue, and its team was able to prevent possibly the biggest hack in crypto history. We all need to learn from this unfortunate situation and realize that not all generators are fit for crypto needs.