Evgen
Verzun

Blog
Founder, Inventor, Crypto- and Cyber- security expert, System and Software Architect
I’m always open to new contacts, ideas and initiatives.
If you have interesting information, idea, proposition, or I can help you, don’t hesitate to contact me.
December 9, 2024
Why Bitcoin Could Hit $250K in 2025: A Data-Driven Analysis
December 9, 2024
Why Bitcoin Could Hit $250K in 2025: A Data-Driven Analysis
The convergence of time-based, macroeconomic, demand-side, and on-chain factors creates a compelling case for Bitcoin to surpass $200,000, potentially reaching $250,000 by 2025
November 29, 2024
Why Nobody Really Wants #Bitcoin at $100,000
November 29, 2024
Why Nobody Really Wants #Bitcoin at $100,000
Bitcoin at $100,000 is more of a psychological milestone than an actual necessity. While it might mark the start of an altcoin season, the turbulence it brings is a high price to pay.
November 11, 2024
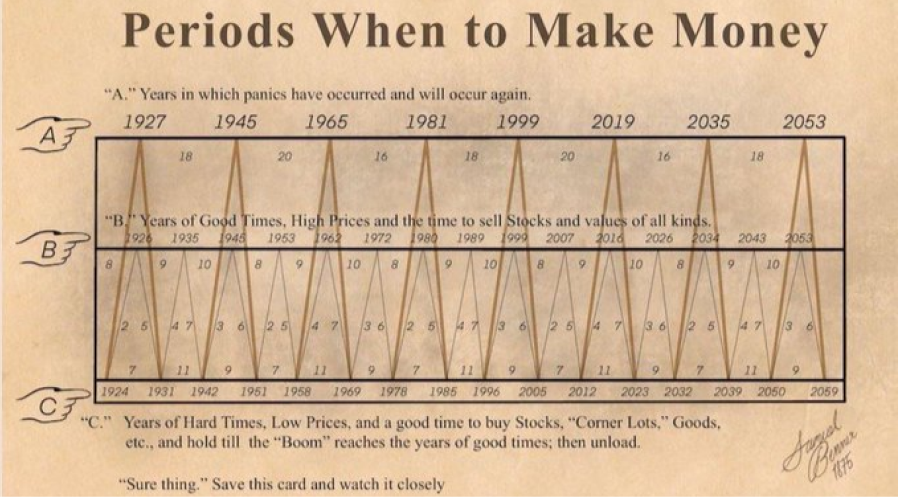
Periods When to Make Money: Fact-Checking Samuel Benner’s Timeless Market Cycle Theory
Samuel Benner’s market cycle theory, dating back to the 1870s, still resonates today. It’s a reminder that while no one can predict every market fluctuation, there are patterns that emerge over time.
November 5, 2024
How a Calculator and a VW Bus Launched Apple
November 5, 2024
How a Calculator and a VW Bus Launched Apple
The story of Apple is one of vision, risk, and resilience. From selling a Volkswagen bus and a calculator to fund their first venture, to building a multi-billion-dollar tech empire
November 4, 2024
Understanding Ethereum’s Future: Breaking Down Vitalik Buterin’s Roadmap
The Merge in 2022 shifted Ethereum to Proof-of-Stake, cutting energy use by 99%. Upcoming phases focus on scaling, fairness, reduced storage needs, data cleanup, and final optimizations to make Ethereum faster, more secure, and globally scalable.
Load more
⨯
My blog couldn't proceed your request right now.
Please try again a bit later.
⨯
Thank you for contacting me!
I will get back to you as soon as I can.
⨯
Contact me
⨯
My blog couldn't proceed your request right now.
Please try again a bit later.
⨯
Thank you for subscribing!
I added you to my emailing list. Will let you know as soon as I have something interesting.
⨯
Subscribe for email updates
Want Blog Updates?